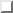 shows how 149.76.12.4, the address of quark, is interpreted differently when the address is taken as an ordinary class-B network, and when used with sub-netting.
shows how 149.76.12.4, the address of quark, is interpreted differently when the address is taken as an ordinary class-B network, and when used with sub-netting.
It makes sense to offer a similar scheme inside the network, too, since it may consist of a collection of hundreds of smaller networks itself, with the smallest units being physical networks like Ethernets. Therefore, IP allows you to subdivide an IP-network into several subnets.
A subnet takes over responsibility for delivering datagrams to a certain range of IP-addresses from the IP-network it is part of. As with classes A, B, or C, it is identified by the network part of the IP-addresses. However, the network part is now extended to include some bits from the host part. The number of bits that are interpreted as the subnet number is given by the so-called subnet mask, or netmask. This is a 32-bit number, too, which specifies the bit mask for the network part of the IP-address.
Figure: Subnetting a class B network
The campus network of Groucho Marx University is an example of such a network. It has a class-B network number of 149.76.0.0, and its netmask is therefore 255.255.0.0.
Internally, GMU's campus network consists of several smaller networks, such as the LANs of various departments. So the range of IP-addresses is broken up into 254 subnets, 149.76.1.0 through 149.76.254.0. For example, the Department of Theoretical Physics has been assigned 149.76.12.0. The campus backbone is a network by its own right, and is given 149.76.1.0. These subnets share the same IP-network number, while the third octet is used to distinguish between them. Thus they will use a subnet mask of 255.255.255.0.
Figure 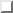 shows how 149.76.12.4, the address of quark, is interpreted differently when the address is taken as an ordinary class-B network, and when used with sub-netting.
shows how 149.76.12.4, the address of quark, is interpreted differently when the address is taken as an ordinary class-B network, and when used with sub-netting.
It is worth noting that sub-netting (as the technique of generating subnets is called) is only an internal division of the network. Subnets are generated by the network owner (or the administrators). Frequently, subnets are created to reflect existing boundaries, be they physical (between two Ethernets), administrative (between two departments), or geographical, and authority over these subnets is delegated to some contact person. However, this structure affects only the network's internal behavior, and is completely invisible to the outside world.